How to Secure Your Contact Form 7 with reCaptcha V2

contactform7withrecaptcha
As we know, WordPress websites have many bot attacks in the form of previous years. While we use a publicly available contact form, we need to make sure there are no spam or bot attacks. Because it’s very easy to detect web scraping and spam about it. To avoid this problem, we use Contact Form 7 with ReCaptcha v2
Contact Form 7 with reCaptcha V2
If you’ve ever used and submitted forms on the internet or website, you should know about reCAPTCHA. This technology developed by Google to identify and recognize the behavior of automated bots. Older versions of reCAPTCHA V2 that require users to complete a riddle or other challenge.
The latest version of reCAPTCHA V3 requires no interaction from users. Monitor user activity transparently in the background to see the difference between human visitors and bots. Since Contact Form 7 supports reCAPTCHA V3, we recommend using this latest version of Captcha as it offers visitors a better user experience.
To set up reCAPTCHA, you’ll first need to generate an API key. To do this, log in to your Google account and go to the reCAPTCHA setup page.

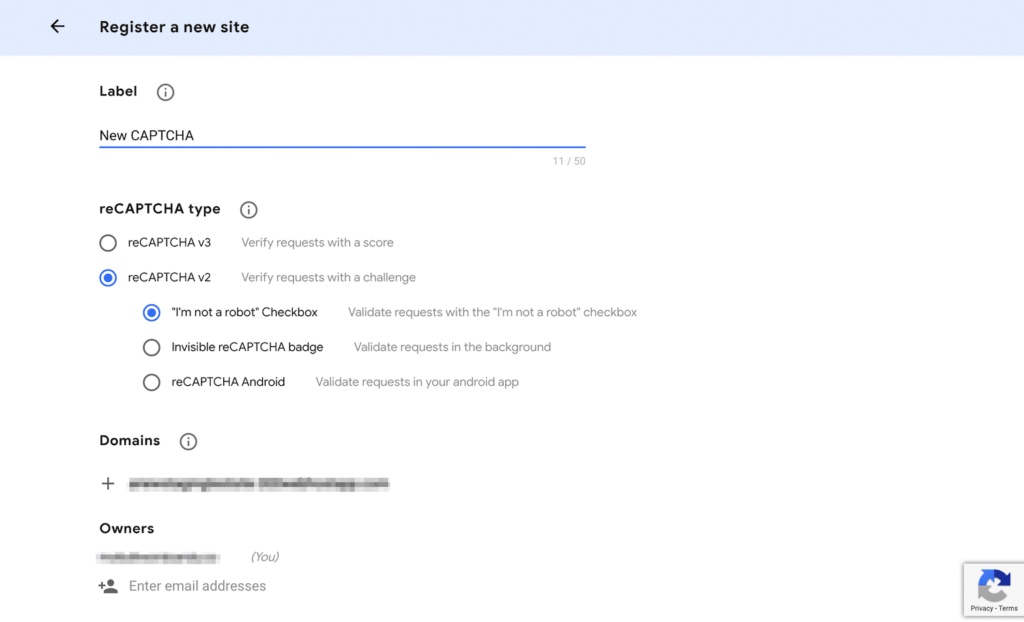
Go through the reCAPTCHA registration form and insert details.
- Label – Choose your own name label.
- reCAPTCHA Type – Contact Form 7 supports reCAPTCHA v3, so select that version.
- Domains – Add your domain here
- Owners – The email address associated with your Google account is added as the owner by default. You can also add another email address
When you have filled out all the options, click Submit. You will then be shown the site-specific “site key” and the “secret key”. Keep these keys in a safe place as you will need to add them. to the contact form 7.
Next, click on the contact in the sidebar of the WordPress dashboard and click on integration. Select the reCAPTCHA option and paste your site key and secret key into the appropriate fields. Finally, click Save Changes to complete the reCAPTCHA integration.
Once you set up reCAPTCHA on Contact Form 7, you will see a reCAPTCHA on your contact form page. This means reCAPTCHA is energetic and protective your contact form from junk mail submissions
Conclusion
Today we learn in this article how to secure our WordPress Contact Form 7 with reCaptcha V2. I hope you understand and it will help protect your form.
Related Articles
Recent Posts
Top 10 ChatGPT Prompts to Learn Anything 10x Faster
Introduction Learning has been transformed by artificial intelligence, which provides resources that enable you to…
Discover the Ultimate Tool for Frontend Designers and Developers
Introduction Even experienced developers may find it difficult to create aesthetically pleasing and useful web…
Git Tag Cheat Sheet
Introduction Git tags are an essential feature of version control systems, offering a simple way…
Understanding Web Storage: Cookies, Local Storage
Introduction The methods that browsers employ to store data on a user's device are referred…
Setting up OpenVPN Access Server in Amazon VPC – AWS
Introduction A well-known open-source VPN technology, OpenVPN provides strong protection for both people and businesses.…
Enhance Error Tracking & Monitoring: Integrate Sentry with Node.js & Express.js
Introduction Integrating Sentry into a Node.js, Express.js, and MongoDB backend project significantly enhances error tracking…